
Businesses are increasingly facing use cases that require the ability to access resources—whether they be applications, files, servers, etc.—across a network. IT administrators need this ability to manage servers and network equipment without physically being in the data center. Call center agents also need it to use server-hosted desktops and applications from thin clients. And, lately, employees likewise need this ability to access corporate files from their homes. This ability, which has grown exponentially in importance throughout the pandemic, is aptly known as remote network access or remote access.
In this article, I’m going to define what remote network access is. Then, I’ll go over some remote access protocols. I’ll also discuss the types of remote access, and talk about other related topics. Let’s start with definitions first.
What Is Remote Network Access?
Remote network access is the ability to access various resources through a network. Those resources can be files, virtual applications, virtual desktops, virtual servers, physical servers, network devices, and even physical desktops, among others. On the other hand, the aforementioned network can be a local area network (LAN), but it can also be a wide area network (WAN) like the Internet.
The ability to remotely access a network has made it possible for people to access resources from any location, even from across the globe. In turn, remote access networks have paved the way for various forms of remote work as well as processes that span multiple locations. By leveraging remote network access, employees can now perform computer-related tasks from just about anywhere.
When you perform remote network access, one or more remote network access protocols may come into play. Let’s talk about those protocols now.
What Are Remote Network Access Protocols?
Remote access protocols are a set of rules that define how data should get transmitted between two devices, usually a client that’s requesting remote access and a host that’s providing remote access. You have several remote access protocols out there. Here are some of the most common ones:
Point-to-Point Protocol (PPP)
PPP is a protocol for direct communications—e.g., leased line or dial-up—hence the term ‘point-to-point’. It can run over a wide range of network communications media including phone lines, serial cables, cellular networks, fiber optic lines, SONET, ISDN, and others.
You can use PPP to enable communications between two computer systems (e.g., one in a branch office and one in your HQ). If you’re an Internet Service Provider (ISP), you can also use it as a way of transmitting IP packets between two modems (e.g., from a home modem to the ISP’s modem).
Internet Protocol Security (IPSec)
IPSec is a set of security protocols for protecting data transmitted over public networks such as the Internet. It supports functions such as data integrity, authentication, and encryption. IPSec is often paired with VPN tunneling protocols such as L2TP (see below). In that case, IPSec provides security to the VPN connection in remote device access.
IPSec can be very secure if you know how to set it up, but it’s also quite difficult to configure. For instance, you need workarounds to make it work with a network address translation (NAT) firewall. Before you roll out an IPSec-enabled solution into production, test for interoperability with existing solutions or solutions you intend to use with it.
Point-to-Point Tunneling Protocol (PPTP)
PPTP is a remote network access protocol based on PPP that’s used for implementing virtual private networks (VPNs). However, it doesn’t support encryption or authentication, so it’s not advisable for production environments.
While it’s true that some businesses still use PPTP (hopefully for non-sensitive remote access connections) due to its speed and compatibility, I suggest you look for other options.
Layer Two Tunneling Protocol (L2TP)
Like PPTP, L2TP is also a protocol used for implementing VPNs. In fact, it traces its roots to the former. It’s slightly more secure than PPTP because it, at least, encrypts its control data. However, it doesn’t encrypt the content itself. That’s why it’s usually paired with IPSec, as the latter provides the needed security.
L2TP/IPSec remote access connections are quite secure, so this is one remote access protocol worth considering if you’re evaluating a VPN solution for remote device access.

Remote Authentication Dial-In User Service (RADIUS)
RADIUS is a protocol for authenticating and authorizing users that are requesting remote network access to certain servers. These servers are usually network access servers (NAS), dial-in servers, VPN servers, wireless access points, and other network access servers. Basically, when a user requests a connection to their NAS, that NAS queries a RADIUS server for authentication and authorization. If the user authenticates, they get access to the resource it has authorization for.
A RADIUS server also can enforce role-based access control. So if you’re trying to incorporate zero-trust and the principle of least privilege in your remote access processes, a RADIUS solution is worth considering.
Terminal Access Controller Access Control System Plus (TACACS+)
Like RADIUS, TACACS+ is a protocol used for authentication and authorization in remote access activities. However, RADIUS is mostly used to authenticate remote users. Conversely, TACACS mostly authenticates administrators that are requesting access to network devices such as routers and switches.
TACACS+ is the more advanced protocol. It provides better encryption functions. It also supports a greater number of protocols. If you’re considering RADIUS as an option, you should look into TACACS+ as well. Basically, evaluate which is the better fit for your business.
Serial Line Internet Protocol (SLIP)
SLIP used to be the de facto standard for transmitting IP packets over a serial link. It was popular during the dial-up era when users would connect to ISPs through a modem. SLIP doesn’t have packet addressing, error checking, and other capabilities that PPP has. As a result, it has gone into obsolescence and has gotten replaced by PPP.
I might be overlooking something, but I can’t think of a network access use case that requires SLIP in this day and age.
Point-to-Point Protocol over Ethernet (PPPoE)
PPPoE is a protocol that encapsulates PPP so that it can get used over ethernet, the technology commonly used for wired LANs and WANs. Note that PPP doesn’t support ethernet on its own. However, with PPPoE, multiple hosts can run PPP sessions over a single ethernet link to connect to a remote site via a common DSL connection.
If you only need one host to connect to your ISP, then PPP will suffice. But if you need multiple hosts (presumably in a LAN) to connect simultaneously, you’ll need PPPoE.
Remote Desktop Protocol (RDP)
RDP is a protocol that allows people to interact with a Windows system from a remote location. It’s often used by home-based or remote workers to access files and applications on their office-based Windows PCs. It’s also used by tech support staff to troubleshoot end-user devices from a remote location.
RDP supports several features that enable remote users to interact with Windows systems as if they’re in the same physical location. You can also use it for copy-pasting content between remote and local environments, printing on local printers from a remote session, and using multiple displays, among other tasks.
Now that you have an overview of the most commonly used remote access protocols, let’s talk about how a typical remote network access process works.
How Does Remote Network Access Work?
When a user retrieves files or loads up a virtual desktop from a remote site, a number of components come into play. Remote network access works through a combination of software, hardware, and a network on which the software and hardware components operate on.
Let’s talk more about each component in detail, starting with software.
Software
Normally, you’ll need software that implements a network access protocol such as PPP, L2TP, RDP, etc. You should install this software (or have it baked in as firmware) on both ends of two devices on which you want to establish some form of remote access. The specific software installed on one device will not always be the same software installed on the other device. For example, in a client-server architecture, the software installed on the client isn’t the same as the software installed on the server. However, they do have to support the same protocol to communicate with each other, so keep that in mind.
Hardware
Unless the other end is a virtual machine in the cloud, that software needs to run on some type of hardware. That hardware can be a PC, laptop, phone, server, router, or some other endpoint device. Regardless of the hardware type, that piece of hardware must have some form of interface, whether built-in or attached (e.g., a network card), that connects it to a network.
Network
This can be practically any network, as long as the hardware and software supports it. So, for example, it can be a LAN, WAN, or the Internet. The network can also be any type of communications medium, e.g., phone lines, serial cables, cellular networks, fiber optic lines, SONET, ISDN—again, provided the hardware and software supports it.
Pro Tips
- When choosing a remote network access software, you should first establish what you want to access. For instance, is it something that requires good security? You’ll need a protocol (e.g., IPsec or SSL/TLS) that supports encryption, authentication, and authorization functionality. Do you want to access entire desktops or applications? You’ll probably need something like RDP.
- It’s a good idea to audit your existing IT infrastructure when thinking about setting up remote network access. You might already have software and hardware that readily supports certain network access protocols. If you really need to purchase additional solutions, try to look for compatible solutions that work with your current infrastructure.
While remote network access is a broad term encompassing different ways of accessing resources over a network, you do have certain types of remote access which are widely used today. Let’s talk about those now.
What Are the Most Common Types of Remote Network Access?
You currently have three different types of remote access that are in popular use today. They are remote access to desktops, remote access to applications, and remote access to files. While you also do have some remote access solutions (e.g., virtual desktop infrastructure—more about this later) that support all three, some solutions (e.g., file transfer servers) only focus on a specific use case. In the following sections, I’ll talk about these types of remote access in more detail. Let’s talk about remote access to desktops first.
Remote Access to Desktops
When used in this context, the term ‘desktop’ refers to an operating system on a physical or virtual machine running in a location geographically separated from the person accessing it. For example, a person in London might be trying to access a Windows desktop in Paris. That person is then supposed to interact with the desktop (e.g., launch Excel and then create or edit a spreadsheet) as if it was running locally.
So how can you remotely access a computer on a different network? While you can use Windows’ built-in RDP protocol for this purpose, you might want to consider other solutions as well. Solutions such as Citrix Virtual Apps and Desktops, VMware Horizon, and Parallels RAS also provide this functionality but offer additional features (e.g., support for non-Windows clients). Of course, these solutions require additional costs, so you should also put that into consideration when picking a solution for accessing a remote desktop.
Remote Access to Applications
This follows a similar concept as the one above, except that, instead of accessing an entire remote desktop, the user only accesses a specific application. The user doesn’t have to, say, launch and navigate a remote Windows desktop to launch Microsoft Excel running on that desktop. Instead, the user simply opens a special client software or a web browser and then launches Excel (running remotely of course) straight from there.
You can use the same solutions that allow you to access remote desktops for this purpose. We mentioned those solutions earlier when talking about remote access to desktops. In most cases, all you need to do is configure them to display specific applications instead of entire desktops.
Remote Access to Files
Not all businesses need to provide users access to remote desktops or remote applications. In many cases, all you’ll want your users to access are company files. For this use case, you don’t need RDP or the other RDP-like solutions I mentioned earlier. What you’ll need instead is a VPN solution.

VPNs enable you to provide users remote network access to files through a secure connection even if they’re doing it over the Internet. Most VPNs come with encryption built-in, so data that you send over it can’t get intercepted and viewed by eavesdroppers. You have several options for securing a VPN connection, but the two most popular ones are SSL and IPSec. That’s what I’ll talk about next.
SSL and IPSec VPNs
Using a VPN is arguably the most widely used method of conducting secure remote network access to files. Of the various options, two stand out—SSL VPNs and IPSec. We have a separate article about SSL VPN vs IPsec, so please click that link if you want to take a deeper dive into that discussion.
The most notable difference between these two is the layers in the OSI model in which they operate. IPSec operates in Layer 3 (Network Layer), while an SSL VPN operates primarily in Layer 4 (Transport Layer) but can also operate in Layers 5-7 (Session, Presentation, and Application Layers).
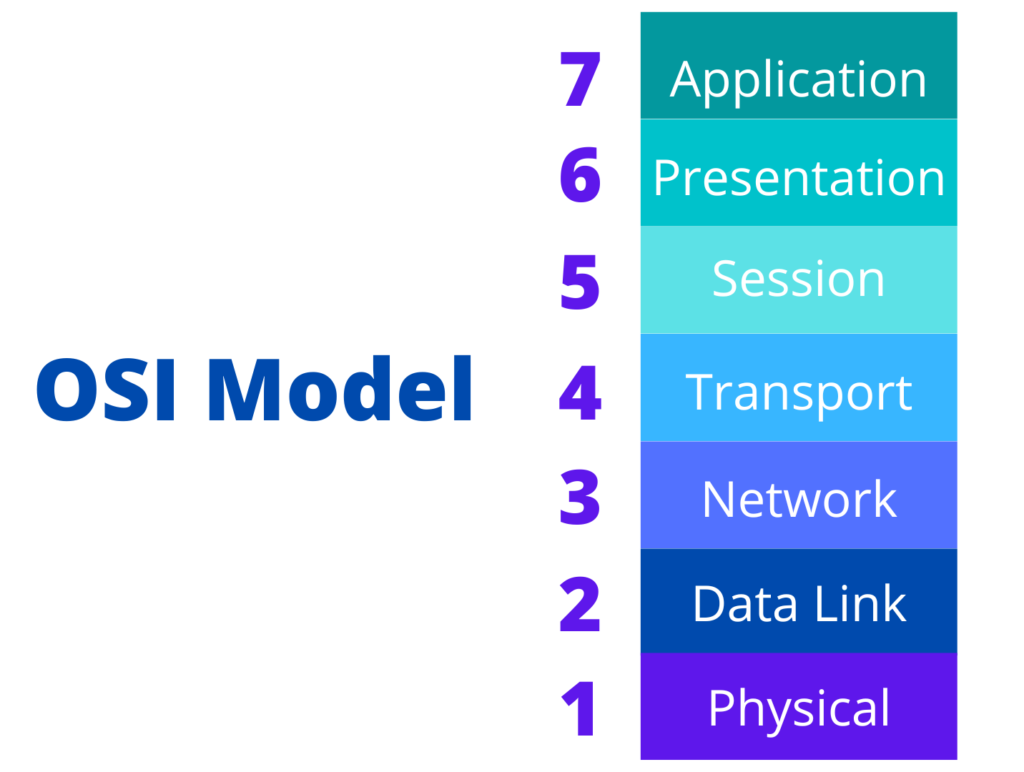
Because of this, SSL VPNs provide security at a more granular level. IPSec secures traffic (through encryption) between VPN clients and a VPN server. Once a VPN client has successfully authenticated, it can access all systems behind that VPN server. On the other hand, SSL VPN secures traffic between VPN clients and individual applications.
Before I end this article, I’d like to share with you a couple of tools that you can use for your remote network access tasks.
3 Remote Network Access Tools Worth Considering
In choosing these 3 remote network access tools, I prioritized security, affordability, and ease of use. So if these qualities are important to you, read on.
1. KerioControl
KerioControl is a 4-in-1 network access tool that incorporates all the capabilities of a next-generation firewall, an intrusion detection system and intrusion prevention system (IDS/IPS), a content filtering solution, and a VPN. Each of these tools addresses different types of threats. That means, with a single tool, you can implement a defense-in-depth security strategy for your remote access processes. You can also use KerioControl to control inbound and outbound network traffic, monitor traffic for threats, prevent users from visiting malicious sites, and protect network access from eavesdroppers.
2. Parallels Remote Application Server (RAS)
Parallels Remote Application Server (RAS) is an easy-to-deploy virtual desktop infrastructure (VDI) solution. It enables you to host operating systems and applications in a central location (e.g., your data center or a public cloud) and make them accessible to users from any device and any location. Because VDI solutions don’t store data on endpoint devices (where they could be at risk when the device gets compromised), you can use Parallels RAS as a secure way of supporting remote work environments.
3. JSCAPE MFT Server
JSCAPE MFT Server is a secure file transfer server that supports multiple file transfer protocols, including FTP, FTPS, SFTP, HTTP, HTTPS, and many others. You can use it for enabling remote users to access files on a server in your on-premises data center. Additionally, you can deploy it on a public cloud and have your users access it from there.
That was a lot of information to take in, wasn’t it? Not to worry, I’ll give you a quick recap now.
Final Words
With the increased adoption of remote work practices, most companies now require some form of remote network access capability. However, before you start building the infrastructure to support that capability, it’s important to understand the basic concepts surrounding it.
In this article, you were introduced to the definition of remote network access, a number of remote access protocols, the main components that make remote access work, common types of remote access, and a couple of remote access tools. The idea was to give you enough information to help you understand what it takes to embark on a remote network access undertaking.
If you want additional explanations regarding some of the terms you encountered in the article, please check out the FAQ and Resources sections below.
FAQ
What is an IDS/IPS?
An intrusion detection system/intrusion prevention system is a security solution that employs several techniques to detect network-based threats and prevent them from entering your network. Some of these techniques include signature-based detection, anomaly-based detection, and stateful protocol analysis. Many solutions only support one capability, i.e., IDS or IPS. KerioControl, which we mentioned earlier, is one solution that supports both.
What does defense-in-depth mean?
Defense-in-depth is a security concept where you protect your infrastructure using multiple layers of security. It’s particularly important in network security since networks are very exposed to a wide variety of threats. No single security solution is ever capable of addressing all of those threats. To address these threats, you can implement a defense-in-depth strategy. You can do this by setting up a firewall, an IDS/IPS, an anti-malware solution, and some form of encryption.
What is content filtering?
Content filtering is a feature in modern firewalls that filter the type of content users access on the web. You can use it to block access to social media websites, pornographic websites, gaming websites, and other types of content that you find offensive or unfit for work environments. Content filtering modules can sometimes inadvertently block legitimate sites, so be mindful of your filtering rules.
What is VDI?
Virtual Desktop Infrastructure (VDI) is a technology that enables you to host desktops, applications, and data in a central location, say an on-premise data center or a cloud infrastructure. It then makes those resources accessible to users through the Internet from practically any endpoint device, including PCs, laptops, thin clients, phones, and tablets.
What is a next-generation firewall (NGFW)?
An NGFW is a type of firewall that adds advanced security features such as deep packet inspection, IDS/IPS, and malware protection with basic features like packet filtering and stateful inspection. It can operate in several layers (e.g., layers 3, 4, and 7) of the OSI model and hence can address a wider range of threats than regular firewalls can.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: Guide for Cloud Network Security
Understand the importance, challenges, and types of cloud network security.
TechGenix: Review on KerioControl with VPN
Weigh the pros and cons of using KerioControl.
TechGenix: Guide for Deploying a VPN on Windows
Learn how to deploy a VPN in a Windows environment.
TechGenix: Article on SIEM Software
Explore the infosec policy-enforcement benefits of a SIEM.
TechGenix: Article on Cloud Computing Trends
Check out the top 6 latest trends in cloud computing in 2022.



